Cybersecurity best practices underpin trust, resilience, and business enablement in today’s technology-driven world, where cloud services, remote work, and IoT devices expand the attack surface and potential consequences of breaches. Moving beyond compliance, organizations should adopt data security best practices that guard sensitive information, reduce risk exposure, and demonstrate governance that customers and partners can rely on, with leadership sponsorship, measurable risk metrics, and alignment to the business risk appetite. Effective security also hinges on everyday actions, including strong password hygiene, robust access controls, and timely patching, all of which contribute to a culture where vigilant behavior is the norm, supported by ongoing coaching and feedback. From phishing awareness to secure configuration and encrypted data transfer, a holistic approach combines people, processes, and technology to deliver sustainable protection without stifling productivity, while governance, regular audits, and security testing stay current. By framing cybersecurity as a strategic capability—supported by online security tips and enterprise cybersecurity practices—organizations can protect assets, earn customer trust, and pursue innovation with confidence, underpinned by clear ownership and governance dashboards.
In the modern digital era, protecting assets hinges on structured information security strategies and proactive risk management that align technology choices with business objectives. Adopting governance-driven approaches to identity and access, encryption, and secure software development creates a resilient foundation while addressing regulatory expectations and stakeholder trust. Another lens emphasizes data protection measures, robust authentication, continuous monitoring, and rapid response capabilities as core components of a comprehensive security program. By speaking in terms like cyber defense guidelines, IT risk management, and zero-trust architectures, organizations can communicate security goals across departments and accelerate safe innovation. Ultimately, aligning people, processes, and technology around these principles helps achieve safer digital operations without slowing down growth.
Cybersecurity best practices for protecting customers and data in an era of cloud and AI
Cybersecurity best practices form the backbone of trust in a technology-driven business landscape. By aligning identity and access management, MFA, and data encryption with enterprise processes, organizations can reduce exposure across cloud services, remote work, and Internet of Things devices. Emphasizing password hygiene and unique credentials for every service helps close the most common attack gap, while data security best practices ensure sensitive information remains protected at rest and in transit.
Beyond technical controls, adopting a culture of proactive risk awareness is essential. Integrating online security tips into daily workflows—such as phishing awareness, secure configuration standards, and routine credential hygiene checks—supports a resilient defense. When security becomes a shared responsibility within the enterprise cybersecurity program, teams gain measurable improvements in data protection, incident response readiness, and customer confidence.
Practical steps for data security best practices and online security tips in modern organizations
Implement practical steps that translate data security best practices into everyday behavior. Start with a tailored patching cadence, enforce strong password hygiene, and apply the principle of least privilege to minimize access. Pair these with robust encryption for data in motion and at rest, and leverage zero-trust concepts to ensure every access request is verified before granting permission. This approach aligns with broader enterprise cybersecurity strategies while keeping users productive.
Regular security training, risk assessment, and governance create a measurable security program. Use security metrics such as mean time to detect and mean time to respond to track progress, and incorporate data protection impact assessments to satisfy privacy and regulatory requirements. By weaving in online security tips and ongoing awareness campaigns, organizations can reduce risk without sacrificing innovation or customer experience.
Frequently Asked Questions
What are the core steps to implement cybersecurity best practices for strengthening data security best practices and online security tips across an enterprise cybersecurity program?
Key steps include: 1) governance and risk assessment to map assets and data flows; 2) strengthen identity and access management with role-based access and password hygiene; 3) enforce multi-factor authentication (MFA) everywhere; 4) maintain timely patching and secure configurations with a zero-trust, least-privilege approach; 5) protect data in transit and at rest with encryption and data loss prevention; 6) secure endpoints and monitor for threats with EPP/EDR; 7) establish continuous monitoring and an incident response plan; 8) invest in security awareness training for ongoing online security tips; 9) ensure reliable backups and disaster recovery readiness; 10) tailor controls to data sensitivity and regulatory requirements. Together these actions reflect cybersecurity best practices, data security best practices, and enterprise cybersecurity strategies.
How can organizations strengthen password hygiene and responsibly roll out MFA within an enterprise cybersecurity strategy while aligning with data security best practices?
Practical steps include: 1) enforce strong password policies (length, complexity, unique credentials) and discourage reuse; 2) adopt passwordless options where feasible to reduce risk; 3) deploy MFA for all critical systems (email, VPNs, admin consoles); 4) centralize IAM with RBAC and regular access reviews; 5) apply zero-trust concepts and least-privilege access; 6) classify data and apply encryption and DLP aligned with data security best practices; 7) provide ongoing security awareness training that reinforces online security tips; 8) track metrics such as MFA adoption and response times to incidents.
| Area | Key Points |
|---|---|
| Introduction / Context | Cybersecurity is a foundational element of trust and resilience. The attack surface grows with cloud, remote work, IoT, and AI tools. Adopting Cybersecurity best practices protects customers, safeguards data, and maintains competitive edge; practical steps cover data security, password hygiene, online security, and enterprise strategies. |
| Threat landscape | Phishing, credential stuffing, and ransomware remain top concerns; attackers increasingly target supply chains, third‑party vendors, and cloud configurations. A single misconfiguration or weak password can trigger a costly incident; success relies on people, processes, and technology plus a security culture. |
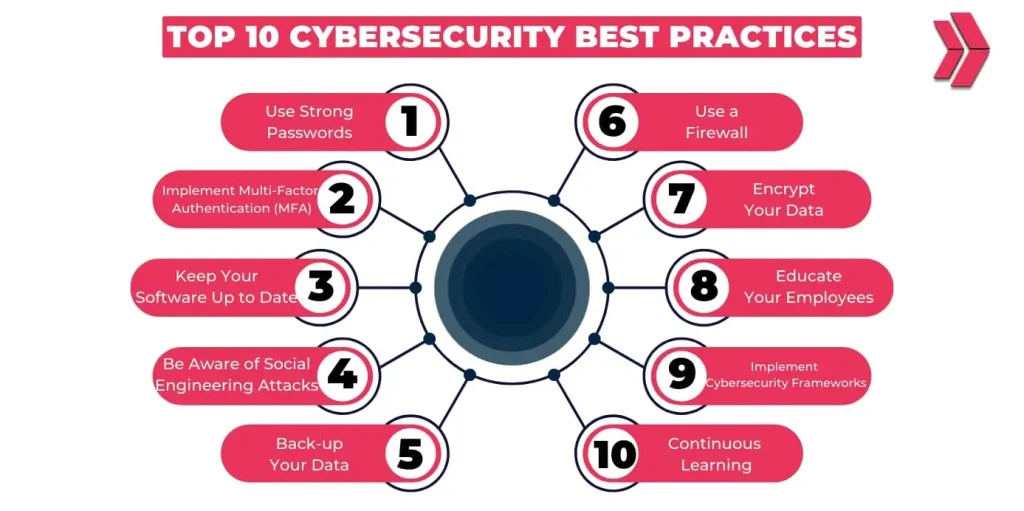
| 1. IAM & password hygiene | Enforce strong passwords, periodic changes, and passwordless options where possible. Use unique credentials; avoid reuse. Implement centralized IAM with RBAC and regular privilege reviews. |
| 2. Multi-factor authentication (MFA) everywhere | Enforce MFA for all critical systems (email, VPNs, admin accounts, cloud consoles). MFA reduces credential theft risk, especially for mobile/remote users. |
| 3. Patching & secure configurations | Maintain timely patches and secure by default configurations. Remove unnecessary services, disable nonessential ports, and employ provenance-based change control to deploy only approved configurations. |
| 4. Least privilege & zero-trust | Provide minimal access; implement network segmentation to contain breaches. Adopt zero-trust networking where every access request is authenticated, authorized, and continuously evaluated. |
| 5. Data in motion & at rest | Use strong encryption for data at rest and in transit. Implement DLP policies and data classification to align controls with data risk. |
| 6. Endpoints & threat monitoring | Protect endpoints with EPP/EDR; keep anti-malware signatures up to date; monitor for anomalies indicating compromise. |
| 7. Monitoring & incident response | Implement continuous monitoring, centralized logging, and timely alerting. Develop an IR plan with roles, runbooks, recovery objectives, and regular tabletop exercises. |
| 8. User education & awareness | Provide ongoing security awareness training (phishing, social engineering, safe browsing). Use simulations to measure awareness and guide training. |
| 9. Backups & disaster recovery | Regular, tested backups; immutable backups when possible; disaster recovery with defined RTOs and RPOs to sustain operations after an incident. |
| 10. Context-tailored controls (privacy) | Align controls with regulations and data sensitivity. Map security controls to regulatory requirements and implement privacy-by-design where appropriate. |
| Practical steps to implement | Carry out risk assessment, establish governance, nurture a security-aware culture, define a budget with metrics (MTTD/MTTR, MFA adoption), and plan regular testing of incident response, backups, and DR. |
| Security as a competitive advantage | Treat security as a product—measurable, user-friendly, and integrated into daily work to earn trust, win business, and reduce downtime. |
| The human factor | Humans cause many incidents; ongoing training, clear policies, and practical workflows help users do the right thing without slowing work. Leadership support and cross-functional collaboration are essential. |
| Future trends | Expect automation, AI-assisted threat detection, broader zero-trust adoption, cloud-native security, SDLC security, and privacy-preserving tech shaping future controls. |
Summary
Conclusion: Cybersecurity best practices are essential for building trust, protecting data, and enabling resilient business operations in today’s technology-driven world. By integrating strong identity and access management, MFA, timely patching, least privilege, data protection, endpoint security, continuous monitoring, and informed user education, organizations can reduce risk and preserve customer confidence. Implementing enterprise cybersecurity strategies may require investment and cultural change, but the payoff is a safer, more agile organization capable of innovating with confidence. Security is a journey, not a destination, and continuous improvement is key to staying ahead of evolving threats.