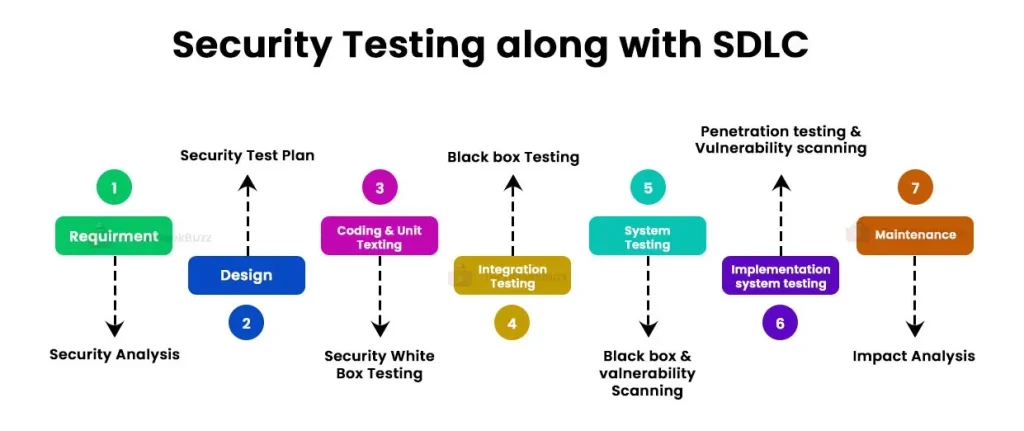
Software security testing is essential in today’s software-driven world. This discipline blends vulnerability assessment, static analysis, and dynamic analysis to uncover weaknesses before they can be exploited. By integrating a risk-based approach and streamlined workflows, teams can catch issues early and reduce remediation costs. A toolkit of Software security testing techniques helps teams map threats and verify protections. Whether you’re building a mobile app, a web service, or an enterprise platform, adopting a structured program builds confidence with stakeholders.
In plain terms, software safety evaluation, application security assessment, and security validation describe the same goal from a different angle. Following Latent Semantic Indexing principles, mention of vulnerability scanning, static analysis, dynamic testing, and threat modeling helps connect related ideas for readers and search engines. These terms frame security work as a continuous, risk-based practice that spans design, development, testing, and deployment. By adopting this broader vocabulary alongside concrete techniques like code review and runtime analysis, teams gain clearer communication and stronger alignment with governance.
Software security testing techniques: a practical framework for secure software delivery
In today’s software-driven world, Software security testing techniques underpin a disciplined approach to finding and fixing weaknesses before they become incidents. By combining broad coverage with deep analysis, teams can assess risk across the user interface, APIs, and data layers, while leveraging vulnerability assessment, static analysis, and dynamic analysis to reveal both obvious flaws and subtle weaknesses in how components interact.
A practical workflow begins with planning security objectives and identifying critical assets, followed by early-stage vulnerability assessment and static analysis during development. As code matures, dynamic analysis exercises the running application in a controlled environment, and targeted penetration testing validates defenses against realistic attack paths. This shift-left mindset helps teams catch issues faster, reduce remediation costs, and build a foundation for secure releases that scale with their tech stack.
To operationalize these techniques, teams should deploy a balanced toolkit that pairs automated scanners with skilled human review. Static analysis supports early bug detection, dynamic analysis reveals runtime issues, and vulnerability assessment provides a broad view of misconfigurations and insecure defaults. By integrating these elements with clear ownership and risk-based alerts, organizations can translate findings into measurable improvements in security posture.
Penetration testing and secure SDLC alignment: turning insights into resilient software
Penetration testing (ethical hacking) plays a critical role in validating the effectiveness of security controls and uncovering business logic flaws that automated checks might miss. By simulating real-world exploits against applications, APIs, and supporting infrastructure, teams gain a realistic view of attacker capabilities and the potential for lateral movement within the system.
Secure SDLC alignment ensures security is not a gate at release but a continuous feedback loop embedded into design, development, and deployment. Threat modeling, security test automation, and repeatable penetration testing workflows integrated with CI/CD help teams detect issues earlier, reduce rework, and accelerate safe releases. When vulnerability assessment and both static and dynamic analyses feed into this ongoing process, organizations can measure progress, enforce governance, and demonstrate tangible risk reduction across releases.
Ultimately, a mature program treats security as an ongoing investment rather than a one-off audit. By combining penetration testing insights with a robust secure SDLC, teams can improve resilience, shorten remediation cycles, and maintain stakeholder confidence as threats evolve and regulatory requirements tighten.
Frequently Asked Questions
What are the essential software security testing techniques and how do vulnerability assessment, static analysis, dynamic analysis, and penetration testing work together?
Software security testing techniques encompass a set of complementary activities designed to identify and remediate weaknesses across an application. A practical core includes vulnerability assessment (broad discovery of weaknesses and misconfigurations), static analysis (reviewing source code without execution to find insecure patterns), dynamic analysis (testing the running application to observe real-time behavior), and penetration testing (adversary-style validation of controls and business logic). Together, these techniques cover different angles of risk, support a shift-left security approach, and help validate fixes before release. Use them in sequence and iteratively within your secure SDLC to reduce risk and improve resilience.
How can I measure and improve the effectiveness of software security testing using vulnerability assessment, static analysis, dynamic analysis, and penetration testing?
To measure effectiveness, track metrics that reflect risk reduction and process efficiency. Useful metrics include the number of unique vulnerabilities discovered per release, time-to-remediation for high-risk issues, the ratio of automated vs. manual findings, and the percentage of code covered by static and dynamic analysis. Integrate vulnerability assessment findings with remediation workflows, and validate fixes through targeted penetration testing and re-running tests in staging. Align security testing with CI/CD and the broader secure SDLC so that ongoing improvements translate into safer software releases.
| Topic | Key Points | Details |
|---|---|---|
| Introduction | Security is a discipline from design through deployment; software security testing systematically evaluates an application to uncover weaknesses; early identification reduces risk and remediation costs; enables safer software and stakeholder confidence. | This guide explains how to build a program adaptable to your tech stack, timelines, and regulatory requirements. It applies to mobile apps, web services, and enterprise platforms, helping you ship safer software and gain stakeholder confidence. |
| Core concepts and why it matters | Breadth and depth across all layers; goal is to reveal a chain of weaknesses that attackers could exploit. | Practitioners rely on a combination of techniques including vulnerability assessment, static analysis, dynamic analysis, and penetration testing, each addressing different angles of risk. |
| Vulnerability assessment | Broad proactive review across the technology stack | Identifies known weaknesses, misconfigurations, and insecure defaults; maps assets; prioritizes remediation based on risk, exposure, and exploitability; combines automated scanners with expert review to minimize false positives and maximize coverage. |
| Static analysis | Inspects code without running the application | Looks for patterns that commonly lead to vulnerabilities such as unsafe input handling, authentication flaws, improper error handling, and insecure data storage. Pairing static analysis results with manual code review validates findings and guides secure coding practices for future iterations. |
| Dynamic analysis | Tests the running application in a controlled environment | Observes real-time behavior, monitors data flow, and detects issues that appear only during execution—such as runtime injections, improper session handling, and memory management problems. Dynamic analysis is especially valuable for web services, APIs, and microservices architectures where interactions are complex and stateful. |
| Penetration testing | Adversary-style assessment that simulates real-world exploits | Validates the effectiveness of security controls, uncovers business logic flaws, and demonstrates how attackers might move laterally within a system. It often combines manual testing with targeted automation to reveal complex attack paths that automated scanners alone could miss. |
| Secure SDLC alignment | Security testing embedded early as a continuous feedback loop | Security testing isn’t a one-time event. When embedded early in the software development lifecycle, it becomes a continuous feedback loop. Practices like secure design reviews, threat modeling, and security test automation help teams catch issues earlier, reduce rework, and accelerate safe releases. |
| Putting the techniques together: workflow | Repeatable workflow aligned with delivery cadences | A mature software security testing program blends the techniques above into a repeatable workflow that aligns with delivery cadences. A typical pattern might look like this: plan security objectives, identify assets and threats via threat modeling, perform vulnerability assessment and static analysis during development, run dynamic analysis and targeted penetration testing on staging, and finally apply verification testing before production. This shift-left approach reduces cost and risk by catching flaws earlier, when remediation is cheaper and faster. |
| Choosing the right tools | No single tool covers every risk; balanced toolkit | A balanced toolkit might include static analysis for early bug detection, dynamic testing for real-time behavior, and a controlled set of automated scanners for continuous monitoring. When selecting tools, consider coverage across your tech stack, CI/CD integration, ease of use, language support, and the ability to tune rules and risk-based alerts to minimize noise. Combine automated checks with human expertise to interpret results, verify true positives, and prioritize fixes by business impact. |
| From findings to fixes | Remediation triage by risk and link findings to concrete actions | Discovery is only valuable if it leads to remediation. As you triage vulnerabilities, categorize them by risk (critical, high, medium, low) and link each finding to concrete actions: code changes, configuration hardening, or architectural adjustments. Track remediation via issue management systems, assign owners, and set realistic timelines. After fixes are implemented, re-run the relevant tests to confirm that the vulnerability is resolved and that no new issues were introduced. This feedback loop is essential to improving the security posture of the product over time. |
| Measuring success | Metrics that matter | To justify investments in software security testing, teams should track measurable outcomes. Useful metrics include: the number of unique vulnerabilities discovered per release, time-to-remediation for high-risk issues, the ratio of automated vs. manual findings, and the percentage of code covered by static and dynamic analysis. Security testing maturity can also be assessed by looking at integration depth with CI/CD, the rate of false positives, and the speed at which security defects move from discovery to fix. Clear, actionable dashboards help stakeholders understand progress and prioritize investments. |
| Challenges and how to overcome them | Obstacles and strategies | Security testing is not without obstacles. Common challenges include scope creep, mounting false positives, and the tension between rapid delivery and thorough testing. To address these issues: start with a risk-based scope, calibrate scanners to reduce noise, and automate repetitive checks so experts can focus on tricky issues. Invest in developer training to promote secure coding practices, and formalize security requirements as part of acceptance criteria. When teams see security as a shared responsibility rather than a gate to slow down delivery, the process becomes easier to maintain and more effective over time. |
| Case for ongoing investment | Culture, automation, and governance | A successful software security testing program grows with the organization. It combines culture (everyone understands security matters), automation (repeatable checks integrated into CI/CD), and governance (clear policies, responsibilities, and remediation processes). The outcome is not a one-off audit but a living program that reduces risk, accelerates secure delivery, and builds trust with users and regulators. |
| Conclusion | Software security testing insights | Software security testing is a critical discipline for modern software development. By combining vulnerability assessment, static analysis, dynamic analysis, and penetration testing within a shift-left, automated workflow, teams can uncover and fix vulnerabilities before they become incidents. The most effective programs treat security as an ongoing investment—an integral part of design, code, testing, and operations—so that every release moves the needle toward safer software and stronger customer confidence. Embrace a holistic approach, tailor your testing strategy to your tech stack, and continuously measure progress to keep your software resilient in a changing threat landscape. |
Summary
Software security testing is a critical discipline for modern software development. By integrating vulnerability assessment, static analysis, dynamic analysis, and penetration testing within a shift-left, automated workflow, teams can uncover and fix vulnerabilities before they become incidents. The most effective programs treat security as an ongoing investment—an integral part of design, code, testing, and operations—so that every release moves the needle toward safer software and stronger customer confidence. Embrace a holistic approach, tailor your testing strategy to your tech stack, and continuously measure progress to keep your software resilient in a changing threat landscape.